Vigenère Cipher Encryption & Decryption Tool
Plaintext
Ciphertext
What is the Vigenère cipher?
The Vigenère cipher is a type of substitution cipher where each letter of the plaintext is shifted according to a key. Unlike the simple Caesar cipher, the Vigenère cipher's main advantage is its resistance to frequency analysis, as it uses multiple alphabets to encrypt the text, significantly increasing the complexity of the cipher.
How does Vigenère cipher encryption work?
- Prepare the Plaintext, Key, and Alphabet:
- Plaintext: The text to be encrypted, e.g., HELLO.
- Key: The word used for encryption, e.g., KEY.
- Alphabet: Defines the supported letter range, e.g., ABCDEFGHIJKLMNOPQRSTUVWXYZ.
- Extend the Key: To match the length of the plaintext, repeat or truncate the key. For example, for the plaintext HELLO, the key "KEY" is extended to "KEYKE".
- Encryption Process:
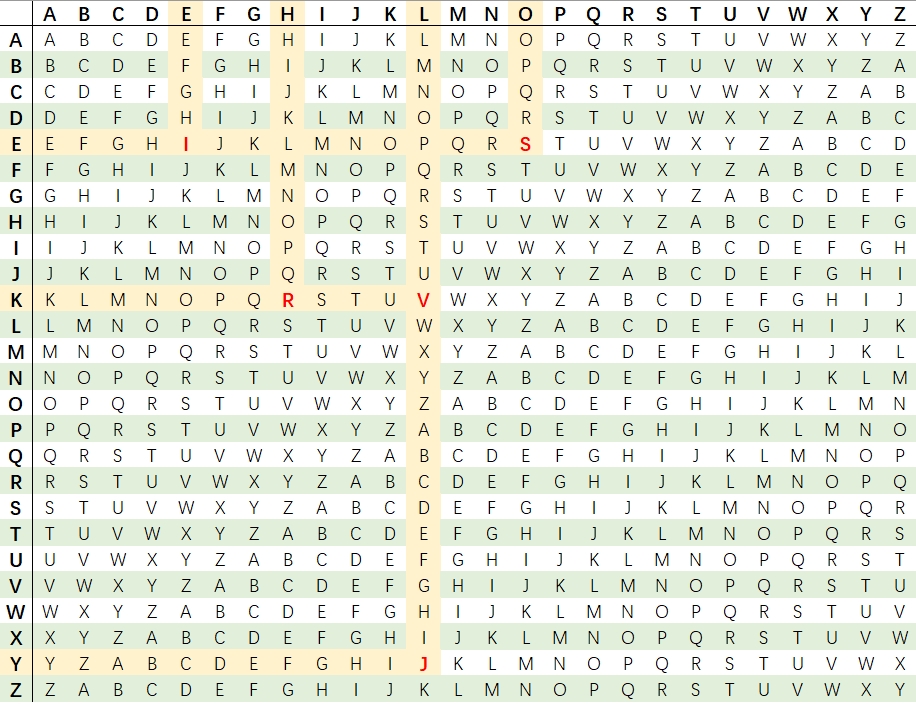
- Use the Vigenère cipher table (which has 26 rows, each starting with a letter from A-Z) to find the encrypted letter.
- The plaintext letter and key letter each determine the column and row in the table. For example, to encrypt H: The plaintext letter H is in the 8th column. The key letter K is in the 11th row. The intersection of the 8th column and the 11th row gives the encrypted letter R.
- Following this pattern:
- E + E → I
- L + Y → J
- L + K → V
- O + E → S
- Thus, the plaintext HELLO encrypts to RIJVS.
How does Vigenère cipher decryption work?

Decryption is the reverse of encryption. It requires using the same key to restore the original plaintext. The steps are as follows:
- Prepare the Ciphertext, Key, and Alphabet:
- Ciphertext: The encrypted text, e.g., RIJVS.
- Key: The same key used for encryption, e.g., KEY.
- Alphabet: The supported letter range, e.g., ABCDEFGHIJKLMNOPQRSTUVWXYZ.
- Extend the Key: Extend or truncate the key to match the length of the ciphertext, e.g., "KEYKE".
- Decryption Process:
- Find the corresponding plaintext letter for each ciphertext letter using the Vigenère cipher table.
- The key letter determines the row in the table. Find the ciphertext letter in the row, and the corresponding column header is the plaintext letter. For example, to decrypt R: The key letter K is in the 11th row. In the 11th row, find the ciphertext letter R. The column header corresponding to R is H, which is the plaintext letter.
- Following this pattern:
- I - E → E
- J - Y → L
- V - K → L
- S - E → O
- Thus, the ciphertext RIJVS decrypts to HELLO.
Advantages and Disadvantages of the Vigenère Cipher
Advantages
- Resistance to Frequency Analysis: Since it uses multiple alphabets for encryption, it is difficult to break by statistical analysis.
- Simplicity: Only one key is needed for both encryption and decryption.
- Multilingual Support: It can be adapted to different language alphabets.
Disadvantages
- Key Management: The key must be kept secret and transmitted securely, or the encrypted content may be easily cracked.
- Weakness to Frequency Analysis: For short keys, attackers can find the key by detecting repeating patterns.
Derived Encryption Methods:
- Autokey Vigenère Cipher: This variation generates the key dynamically by using the first few characters of the plaintext as part of the key, avoiding repeating patterns.
- Beaufort Cipher: An improvement on the Vigenère cipher that uses different shift rules for encryption.
- Playfair Cipher: Uses a 2D letter matrix to further increase encryption complexity.
How to Use the Vigenère Cipher Tool?
- Enter the Content: To encrypt, type the content to be encrypted in the "Plaintext" box. To decrypt, type the content to be decrypted in the "Ciphertext" box.
- Custom Key: Users can input any length key, which directly determines the shift rules for encryption and decryption.
- Custom Alphabet: The tool supports different language alphabets (such as English, French, German, etc.). Users can also manually input a custom alphabet to adapt to special needs.
- Unknown Character Retention Option: Choose whether to retain unrecognized characters in the ciphertext (such as punctuation marks, spaces, etc.).
- View Results: The tool will update the encryption or decryption results in real-time, displaying them in the corresponding box.