ADFGVX and ADFGX Cipher
Plaintext
Ciphertext
| A | D | F | G | V | X | |
|---|---|---|---|---|---|---|
| A | A | B | C | D | E | F |
| D | G | H | I | J | K | L |
| F | M | N | O | P | Q | R |
| G | S | T | U | V | W | X |
| V | Y | Z | 0 | 1 | 2 | 3 |
| X | 4 | 5 | 6 | 7 | 8 | 9 |
What is the ADFGVX Cipher?
The ADFGVX cipher is a polyalphabetic substitution cipher that was originally used by the German military during World War I. It combines both substitution and transposition principles and utilizes a 6×6 matrix to encrypt letters. In this cipher, letters are replaced by a pair of characters that correspond to the rows and columns of the matrix. The name "ADFGVX" comes from the six letters used in the matrix (A, D, F, G, V, X), which represent the rows and columns, as shown below:
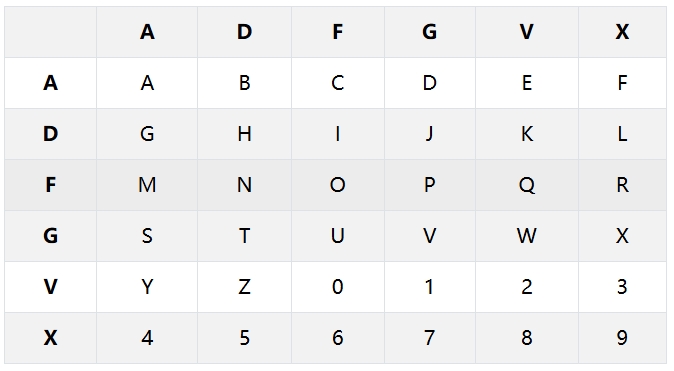
In the ADFGVX cipher, each plaintext letter is first replaced with a pair of letters that represent the row and column positions, based on a predefined alphabet. For example, the letter "M" corresponds to the row-column code "FA". The second step in encryption is to rearrange these letter pairs according to a keyword, resulting in the final ciphertext.
Comparison between ADFGVX and ADFGX Ciphers
While both ADFGVX and ADFGX belong to the same cipher family, there are key differences between the two. These differences mainly lie in the structure of the alphabet and the number of characters used, which in turn affect the complexity of encryption and decryption as well as the suitability for different use cases.
| Feature | ADFGVX | ADFGX |
|---|---|---|
| Alphabet Size | 6×6 matrix, 36 characters (letters + numbers) | 5×5 matrix, 25 characters (letters only) |
| Row/Column Code | A, D, F, G, V, X | A, D, F, G, X |
| Encryption Complexity | Higher, supports more types of characters, stronger security | Lower, handles only letters, simpler encryption |
| Security | Stronger, suitable for high-security needs | Weaker, suited for simpler encryption |
| Use Cases | Used for complex information encryption, such as military communications | Used for simpler, letter-only encryption |
How Does the ADFGVX and ADFGX Cipher Encrypt?
- Prepare the Plaintext: Remove any non-alphabet characters (such as spaces, punctuation, etc.).
- Construct the Alphabet Matrix: Set up the alphabet, creating the ADFGVX or ADFGX matrix based on the chosen alphabet.
- Substitute Plaintext Characters: For each letter in the plaintext, locate its corresponding row and column in the matrix and replace it with a pair of letters representing its position.
- Construct the Key Table: Using the keyword, construct a table by writing the row-column codes into it, filling in the rows.
- Sort the Table: Reorganize the columns based on the alphabetical order of the keyword letters.
- Generate the Ciphertext: Read the table column by column to obtain the final ciphertext.
Example
Assume the plaintext is: "HELLO WORLD", using the default alphabet (A-Z, 0-9) in ADFGVX mode, and the keyword "KEYWORD":
1. Construct the Alphabet Matrix
| A | D | F | G | V | X | |
|---|---|---|---|---|---|---|
| A | A | B | C | D | E | F |
| D | G | H | I | J | K | L |
| F | M | N | O | P | Q | R |
| G | S | T | U | V | W | X |
| V | Y | Z | 0 | 1 | 2 | 3 |
| X | 4 | 5 | 6 | 7 | 8 | 9 |
2. Substitute Plaintext Characters
- H → (D, D)
- E → (A, V)
- L → (D, X)
- L → (D, X)
- O → (F, F)
- W → (G, V)
- O → (F, F)
- R → (F, X)
- L → (D, X)
- D → (A, G)
3. Build and Fill the Key Table
| K | E | Y | W | O | R | D |
|---|---|---|---|---|---|---|
| 3 | 2 | 7 | 6 | 4 | 5 | 1 |
| D | D | A | V | D | X | D |
| X | F | F | G | V | F | F |
| F | X | D | X | A | G |
4. Sort the Table
| D | E | K | O | R | W | Y |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| D | D | D | D | X | V | A |
| F | F | X | V | F | G | F |
| X | F | A | G | X | D |
5. Generate the Ciphertext
Read column by column to obtain the final ciphertext: DFDFXDXFDVAXFGVGXAFD.
How Does the ADFGVX Cipher Decrypt?
The decryption process mirrors the encryption steps. After obtaining the row-column coordinates, you need to fill them into a table according to the alphabetical order of the keyword (A-Z). Pay attention to whether the table can be completely filled. If not, note which cells are left empty. Once filled, restore the table to the original order of the keyword. Finally, read across the rows (horizontally) in pairs to retrieve the row-column coordinates. Using these coordinates and the alphabet matrix, the original plaintext is restored.